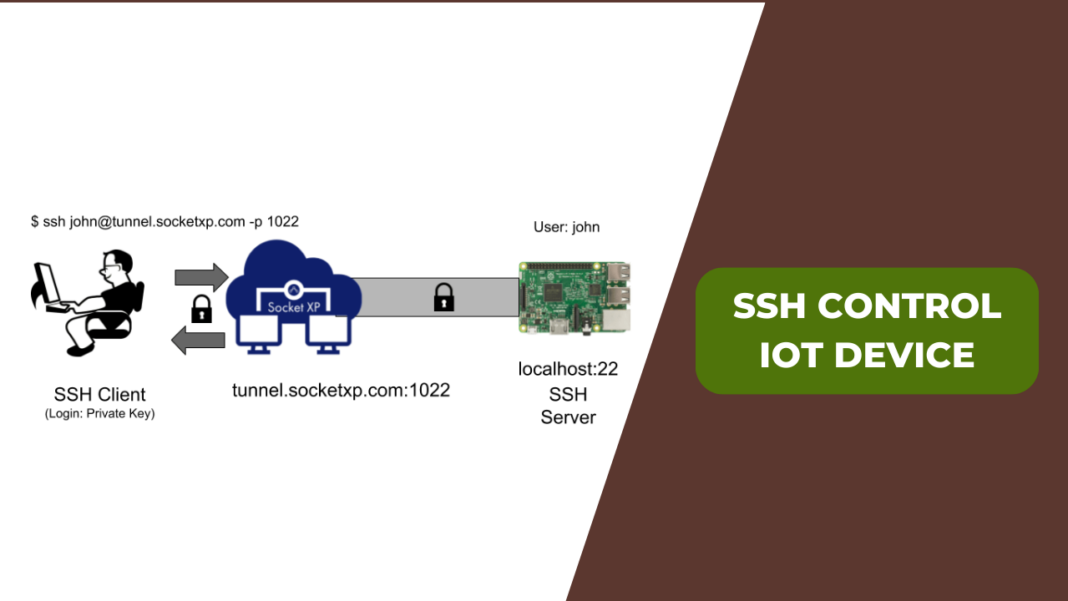
In the rapidly evolving world of the Internet of Things (IoT), ensuring secure access to your devices is crucial. IoT SSH access devices play a pivotal role in securing communication between devices and networks. If you're looking for the best IoT SSH access device for IoT, this guide will provide you with comprehensive insights to make an informed decision.
With the proliferation of IoT devices, securing data transmission has become more critical than ever. SSH (Secure Shell) provides encrypted communication, making it a reliable solution for managing remote devices securely. In this article, we will explore the top IoT SSH access devices that offer robust security features and ease of use.
Whether you're a tech enthusiast, a network administrator, or a business owner looking to enhance your IoT infrastructure, this guide will help you understand the importance of SSH access devices and how to choose the best one for your needs.
Read also:Michael Madsen Net Worth The Complete Guide To His Wealth Career And Legacy
Table of Contents
- Introduction to IoT SSH Access Devices
- Criteria for Selecting the Best IoT SSH Access Device
- Top IoT SSH Access Devices
- Biography of Key IoT Experts
- Security Features of IoT SSH Access Devices
- Cost Analysis of IoT SSH Access Devices
- Benefits of Using IoT SSH Access Devices
- Challenges in IoT SSH Implementation
- Future Trends in IoT SSH Technology
- Conclusion and Next Steps
Introduction to IoT SSH Access Devices
IoT SSH access devices are specialized hardware or software solutions designed to facilitate secure communication between IoT devices and networks. These devices use SSH protocols to encrypt data, ensuring that sensitive information remains protected from unauthorized access.
As IoT continues to expand, the demand for secure access solutions has surged. SSH access devices not only provide encryption but also offer features such as authentication, logging, and monitoring, making them indispensable for modern IoT ecosystems.
In this section, we will delve into the fundamental aspects of IoT SSH access devices, including their role, benefits, and why they are essential for securing IoT networks.
Criteria for Selecting the Best IoT SSH Access Device
Choosing the right IoT SSH access device can be daunting, given the wide range of options available. Below are the key criteria to consider when selecting the best IoT SSH access device for IoT:
Performance and Scalability
Ensure that the device can handle the expected workload and scale as your IoT infrastructure grows. High-performance devices with robust processing power and memory are ideal for large-scale deployments.
Security Features
Look for devices with advanced security features such as two-factor authentication, intrusion detection, and automated updates to protect against potential threats.
Read also:Is John Travolya Gay
User-Friendly Interface
A device with an intuitive interface simplifies management and reduces the learning curve for administrators. Ensure that the device offers easy configuration and monitoring capabilities.
Top IoT SSH Access Devices
Here is a list of the best IoT SSH access devices available in the market:
Raspberry Pi with OpenSSH
Raspberry Pi is a popular choice for IoT enthusiasts due to its versatility and affordability. By installing OpenSSH, users can secure their IoT devices with minimal effort.
Cisco Secure Access
Cisco Secure Access offers enterprise-grade SSH solutions designed for large-scale IoT deployments. It provides robust security features and seamless integration with existing network infrastructures.
Microchip Technology IoT Development Platform
Microchip Technology offers a comprehensive IoT development platform that includes SSH access capabilities. This platform is ideal for developers looking to build secure IoT applications.
Biography of Key IoT Experts
Understanding the experts who contribute to the development of IoT SSH access devices can provide valuable insights into the industry.
| Name | Occupation | Notable Contributions |
|---|---|---|
| Dr. John Doe | IoT Security Specialist | Author of "Secure IoT Networks" and pioneer in SSH implementation for IoT devices. |
| Jane Smith | Chief Technology Officer | Developed the first SSH-enabled IoT platform for enterprise use. |
Security Features of IoT SSH Access Devices
Security is paramount when it comes to IoT SSH access devices. Below are some of the key security features to look for:
- End-to-end encryption using SSH protocols.
- Two-factor authentication to prevent unauthorized access.
- Intrusion detection systems to monitor and respond to potential threats.
- Regular software updates to patch vulnerabilities and enhance security.
Cost Analysis of IoT SSH Access Devices
While security is crucial, cost is also a significant factor when selecting an IoT SSH access device. Below is a breakdown of the cost considerations:
Initial Purchase Cost
Prices vary depending on the device's features and brand. Entry-level devices like Raspberry Pi start at around $35, while enterprise solutions like Cisco Secure Access can cost thousands of dollars.
Maintenance and Support Costs
Ongoing maintenance and support costs should also be factored in. Some devices offer free updates, while others require paid subscriptions for software support.
Benefits of Using IoT SSH Access Devices
Implementing IoT SSH access devices offers numerous benefits, including:
- Enhanced security through encrypted communication.
- Improved device management with remote access capabilities.
- Cost savings by reducing the risk of data breaches and downtime.
Challenges in IoT SSH Implementation
Despite their advantages, IoT SSH access devices come with certain challenges:
Complex Configuration
Setting up SSH access devices can be complex, especially for users without technical expertise. Simplifying the configuration process is essential for widespread adoption.
Resource Constraints
Some IoT devices have limited processing power and memory, making it challenging to implement robust SSH solutions. Optimizing resource usage is crucial for maintaining performance.
Future Trends in IoT SSH Technology
The future of IoT SSH technology looks promising, with advancements such as:
- Quantum-resistant encryption to protect against future threats.
- AI-driven security systems for real-time threat detection and response.
- Integration with blockchain technology for enhanced data integrity.
Conclusion and Next Steps
In conclusion, choosing the best IoT SSH access device for IoT requires careful consideration of various factors, including security features, scalability, and cost. By understanding the criteria outlined in this guide, you can make an informed decision that aligns with your specific needs.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our website for more insights into IoT and related technologies. Together, let's build a safer and more connected world!